Sometimes when dealing with certificates, a problem occurs when the certificate does not have a private key assigned to it.
In regards to Lync for instance, it’s not possible to assign the certificate to any services when the private key is missing. The solution to this problem is rather simple, and well documented in Microsoft TechNet but i still choose to write a post about it i case someone stumbles accross it and finds it useful.
Import the certificate in the MMC certificate Snap-In as you would do with any other certificate for the computer account. The certificate shows up in the Personal certificate store. Then doubleclick the certificate in the Personal view, and select the Details tab.
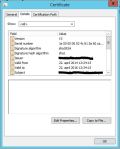
- Copy the serial number from the cerificate properties.
- Start a command prompt with elevated rights and type the following command:
certutil.exe -repairstore my “serialnumber of the certificate” - Refresh the Personal certificates view, and you will see that the certificate has now been assigned a private key.
Ready to go.
Update:
Just to make it clear, as it’s correctly pointed out by Lasse in the comments, it’s not possible to restore a private key to a certificate without actually having the private key in your cert store.