Recently I came accross a problem that I’ve never had before. The environment is a mixed environment of Windows Server 2008, 2008 R2 and Windows Server 2012.
I installed Lync Server 2013 FE on a standard Windows Server 2012(which I’ve done a couple of times before with no problems at all). Requested certificates from internal CA server, all went as expected. The Lync server fired up, and all services came online. No problems so far.
Then I tried to log on from a Client, and nothing happened. I immediately checked the Event logs to see what was wrong, and came accross this event:
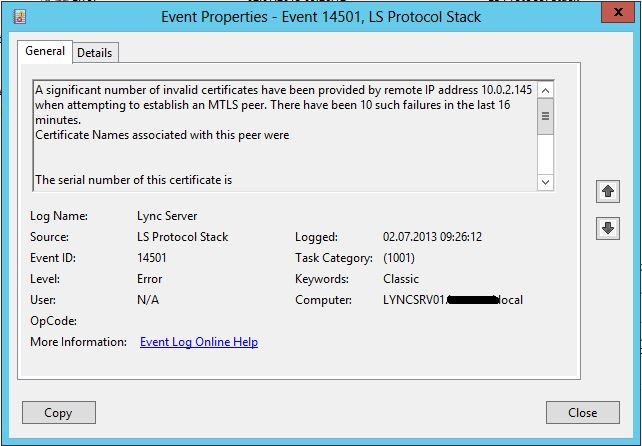
The text is as follows:
A significant number of invalid certificates have been provided by remote IP address 10.0.2.145 when attempting to establish an MTLS peer. There have been 10 such failures in the last 16 minutes.
Certificate Names associated with this peer were
The serial number of this certificate is .
The issuer of this certificate is The specific failure types and their counts are identified below. Instance count
– Failure Type 10 0x80090331(SEC_E_ALGORITHM_MISMATCH)
Turns out Lync server 2013(or the Windows Server 2012) is not very happy with the MD5 signature algorithm used by the local CA servers root certificate.
Solution:
Change the CA’s signature algorithm, the one that the CA uses to sign its issued certificates after installation (sure, you cannot change the algorithm with which the CA’s own certificate is signed). This can be done in registry, in HKLM\System\CurrentControlSet\Services\CertSvc\Configuration\…\CSP. There is the CNGHashAlgorithm (or HashAlgorithm) value, that contains the current signature algorithm. Change it to SHA1 and restart the CA service, from that point on, CA will be signing with the new algorithm. Also, you would have to update the internal root certificate With the New algorithm(recreate it).
Keep in mind that when this is done, you would have to make sure the new root certificate is published in your organization(most common way is by GPO’s). Also, consider the size of your organization and number of computers the certificates are deployed to(in my case, the organization was rather small and the number of certificates issued was very low).